Fencing is a barrier established to protect a certain range of objects from being infringed, and to some extent it has a protective effect, but it cannot be completely prevented. Traditional fences are used to increase or add dangerous touch objects to increase the safety, but it will affect the appearance, can not take the initiative to knock back, but also bring inconvenience to the characters in the fence. The electronic fencing used pulsed electron detection and found that the intruder actively repulsed. The network electronic fence implements the networking technology, and it can also record the defensive screen so that the managers in the area can understand the situation faster and more timely.
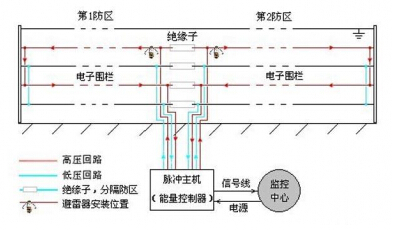
An electronic fence is an active intrusion prevention fence that counters an intrusion attempt, repels an intruder, delays the invasion time, and does not threaten human life. It sends the intrusion signal to the security department monitoring equipment to ensure that the management personnel Can understand the situation of the alarm area in time, and quickly handle it.
The network electronic fence is just like a fence. It is a video linkage alarm system. The network electronic fence is a new-generation electronic fence system that combines traditional electronic fence technology and network technology. It is mainly composed of an electronic fence host, intelligent control keyboard and management. Software components, users can monitor the electronic fence through the network to achieve real-time user information transmission, data interaction and remote monitoring capabilities.
In the cyber electronic fence zone, when someone illegally climbs the fence or damages, the warning light will immediately give warning light and sound to drive away. The pulse electronic fence host takes the initiative to complete the transmission immediately after receiving the signal from the front end. The camera in the corresponding area is quickly adjusted to the preset position, and the linked LED lights illuminate the invaded area, ensuring that even in the dark night, the clear alertness screen can be transmitted to the post and management center. The security management platform software in the management center pops up an alert prompt window, and sends an alarm message to the designated person's mobile phone through the short message module. The on-duty personnel responded immediately after receiving the alarm and arranged for the personnel to go to the scene to handle.
Linkage video surveillance restore field security management platform software with alarm records query, site image review and other functions, to provide scientific basis for future intrusion events. In addition, the software can also realize cross-regional remote control and hierarchical management, so that multiple controlled sites and upper management departments form a system that is closely linked to facilitate unified command and unified management.
Compared to traditional electronic fences, network electronic fences have the following advantages:
All alarm signals and status signals of the centralized platform are connected to the terminal controller of the management center through the module. The network electronic fence will be integrated and compatible with various security subsystem devices to form a unified management platform.
Hierarchical management system can also be divided according to the actual situation of authority, to achieve hierarchical management and adjustment: such as arming and disarming the electronic fence, high and low voltage conversion; preset camera settings, camera switching and so on. Breakthrough regional status query alarms and equipment information are converted to TCP/IP network standard data packets are transmitted to the management computer. Authorized administrators can not only view them locally, but also visit other terminals through the network, breaking the geographical barriers. Real-time control, corresponding to the timely network electronic fence system can achieve 24-hour real-time data acquisition and control. In the face of unexpected situations, the system proactively reminds management personnel to implement processing, which greatly enhances processing efficiency and reduces the risk of loss. Network E-Fence Model Architecture Analysis Network E-Fence model architecture can be divided into physical layer, sensing layer, control layer, and network. Layers and application layers have a total of five layers.
The physical layer is the hardware of the security equipment installed at the site, such as the electronic fence front-end system, video surveillance camera, alarm lights, LED lights, patrol collection points, etc. The main role is to carry the detection signal, blocking, deterrence intrusion By.
Various types of device sensors and transmission cables form a sensing layer and have functions of analyzing and detecting signals, identifying alarm information, and transmitting signals.
The control layer adopts the data bus technology, including the control keyboard, alarm host, hard disk recorder, etc., to perform local integration and management control of the front sensor layer equipment, and implements the control of arming and disarming, working mode adjustment, alarm signal analysis and processing, and signal uploading. Features.
The network layer is the basis for providing network communication support for the system equipment and realizes the information transmission of the front-end alarm equipment. According to the different needs of users, various network structures such as a local area network, a wide area network, and an Internet may be adopted.
The application layer is combined with the user's specific application scenarios to perform proper integration, linkage, analysis, and storage.
When someone illegally climbs over the wall or destroys it, the warning light will immediately give warning light and sound to drive it away. The pulse electronic fence host takes the initiative to complete the transmission immediately after receiving the signal from the front end. The camera in the corresponding area is quickly adjusted to the preset position, and the linked LED lights illuminate the invaded area, ensuring that even in the dark night, the clear alertness screen can be transmitted to the post and management center.
The security management platform software in the management center pops up an alert prompt window, and sends an alarm message to the designated person's mobile phone through the short message module. The on-duty personnel responded immediately after receiving the alarm and arranged for the personnel to go to the scene to handle.
The security management platform software has the functions of alarm record query, on-site image review and so on, which provides scientific basis for handling intrusion events later.
In addition, the software can also realize cross-regional remote control and hierarchical management, so that multiple controlled sites and upper management departments form a system that is closely linked to facilitate unified command and unified management.
Attachment: Installation Notes for Electronic Fence:
1, In order to reduce the risk of electric shock, please do not get the warning signs while working in the electronic fence, and stop other people from moving the warning signs.
2. Do not use damaged wires, especially those with spikes, to prevent injury to humans and animals. 3. When charging a maintenance-free lead-acid battery or other dry batteries, remove the battery and recharge it. Charge the battery directly on the electronic fence, which will cause damage to the battery and the electronic fence host.
4, can not be the two sets of electronic fencing host power supply to the same fence, this will be due to electronic fence host issued by the high-voltage pulse is not consistent with the host damage, but also easily lead to human and animal casualties.
5, It is forbidden to modify the internal circuit of the electronic fencing mainframe by oneself, or to replace the electronic components. This can easily cause the machine to malfunction or cause harm to human life.
6. It is strictly forbidden to touch or approach the electronic fence during thunderstorms to prevent the occurrence of a lightning strike. For all electronic fences, whether it is mine or not, this item must be prohibited.
7. Inform all the personnel who manage the fence how to cut off the output of the electronic fence host to prevent the occurrence of an emergency. In addition, how to cut off the operation guide of the electronic fence host should be placed on the conspicuous place of the electronic fence host. 8 It is forbidden to use the adaptor without commercial power to the adapter of 12V DC. Host power supply, this is easy because the adapter itself fails to cause the host output voltage is too high, insulation failure occurs.
9, After the installation, please confirm whether the host is working properly. If the host's power is on, it means that it is working properly. Please use it with confidence. Do not touch the fence after starting up.
10. It is forbidden for infants and young children. Pregnant women touch electronic fences. No matter whether they have conditions, they must prevent such personnel from approaching the electronic fence. Otherwise, they cannot install such equipment. 11 They must prevent visible warning signs from being placed beside the electronic fence host and place warning signs at the fence. .
12, grounding must be reliable, compact, grounding system must be far away from the living area.
13, It is forbidden to dismantle the electronic fence host privately. It is forbidden to replace the components without authorization and contact the supplier in case of any problem.

 Mr. Alex Wang
Mr. Alex Wang